- By Javeria
- January 10, 2024

Nowadays, cloud Computing is being introduced and marketed with many attractive features, such as reduced costs, and relief from managing complex IT infrastructure.
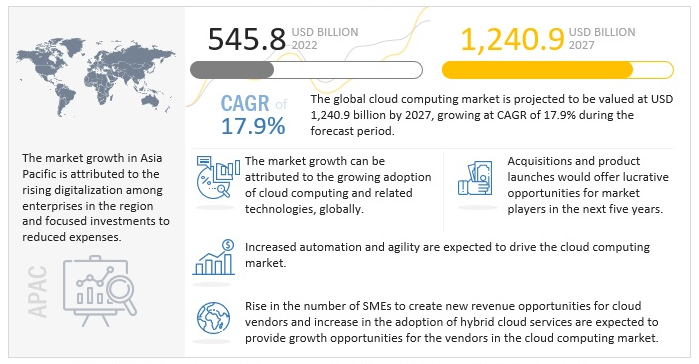
Several organizations are moving to the cloud as part of embracing digital transformation. The global market for cloud computing is expected to reach $545.8 billion in 2022 and $1240.9 billion in 2027.
Cloud computing threats pose significant risks and vulnerabilities, despite the many advantages it offers in terms of flexibility and scalability. You need to be aware of it to avoid any costly mishaps. Before discussing them in detail, let’s briefly examine the concept of the cloud.
Cloud is a service that provides its users with on-demand software and hardware functionalities through the Internet. It means that one could easily avail hardware and software resources such as storage and computing power whenever needed using online connectivity. The Cloud services provider will store the essential hardware and software in their data centers. They purchase, operate, and maintain such resources so that users do not need to buy and install them.
The insider threats are amplified in cloud servicing because the cloud service provider has its staff and its own data centers in different geographical locations on the planet. Employees who are working at a cloud service provider may have complete access to company resources.

Therefore, they need to take complete security measures to track employee actions like viewing a customer’s data. Cloud service providers that don’t follow the best security guidelines, run the risk of their employees and gathering confidential information from customers without being detected.
Cloud users avail software interfaces and APIs to access and manage cloud services. The APIs need to be secured because they play an essential role in the management and monitoring of the services running in a cloud environment. The security and availability of cloud services depend upon the security of the APIs. So, it needs to include the features of authentication, access control, encryption, and activity monitoring.
APIs must be designed to protect against both accidental and malicious attempts. If a cloud service provider depends on a weak set of APIs. Many security issues will be raised related to confidentiality, integrity, and accountability. These issues may include malicious or unidentified access, API dependencies, and inflexible access controls.
Threats related to data deletion exist because the user has reduced visibility into where their data is physically stored in the cloud and also limited ability to validate the secure deletion of their data and information.
In addition, deletion procedures may differ from provider to provider. Organizations may not be able to verify that their data was securely deleted and that miscellaneous files are not available to attackers. This threat increases as consumers use multiple cloud services.
Hosting private data with cloud service providers includes the transfer of a significant amount of the organization’s control over data security to the provider. Make sure your cloud computing threat service provider knows your organization’s data privacy and security needs.

Also, make sure your cloud provider is aware of data security, privacy rules, and regulations that apply to your company. For example, HIPAA, the Federal Information Security Management Act of 2002 (FISMA), or the privacy contemplations of the Gramm-Leach-Bliley Act.
A major risk to businesses in the cloud computing environment is the loss of internet connectivity. Ask your cloud provider what controls are available to ensure internet connectivity. If a vulnerability is recognized, you may have to terminate all access to the cloud provider until it is fixed.
Hosting your computing resources and data with a cloud service provider makes the cloud provider’s disaster recovery capabilities extremely important. Know your cloud provider’s disaster recovery capabilities and ask your provider if they’ve been tested.

While companies around the world enjoy the benefits that cloud computing brings, security in the cloud is a key challenge. Many vulnerabilities in the cloud still exist and opportunists continue to exploit these security loopholes. Companies operating in the cloud are taking big risks if they are unaware of or do not take sufficient action to neutralize the threats that come with it.
If you have any comments, queries, or suggestions regarding this article, please state them in the comments section below. Thanks for reading.